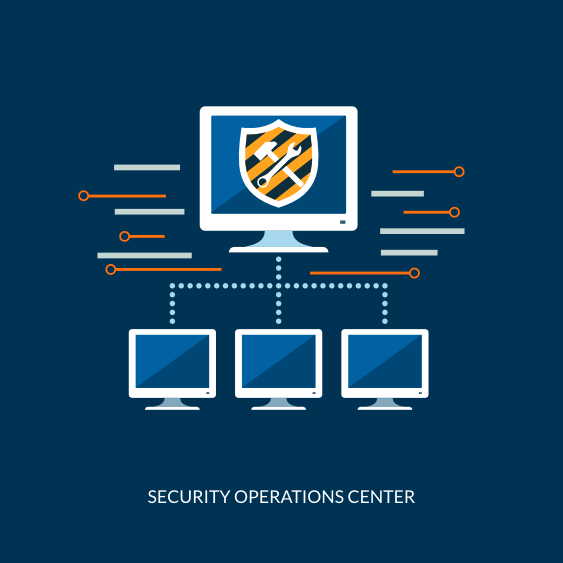
Vital to foundational cyber security are the people, processes and technology that support the Information Security function. These are most effective when they are centralized, structured and coordinated on an organizational and technical level- which is why a Security Operations Center (SOC) is a valuable starting point.
A well-functioning SOC can form the heart of effective cyber threat detection, helping to leverage cutting edge data processing technology in order to secure the enterprise information systems from attackers. It can enable information security functions to respond faster, work more collaboratively, and share knowledge more effectively.
However, with the exponential growth of the digital world the threats also continue to rapidly evolve both in sophistication and in scale. This massive digital threat expansion highlights the need to protect organizations’ intellectual property, operations, brand and shareholder value, in addition to their customers’ data. The demand for damage prevention is now more apparent than ever across all business sectors.
We are now seeing the emergence of the third generation of SOCs; converging specialist skillsets from disciplines related to cybersecurity, threat intelligence, data science and cyber analytics into advanced SOC ecosystems, where the whole is greater than the sum of its parts.